What Is Identity Security ?
Every organization relies on technology to operate, and securing access to that technology is essential. Identity security (also known as identity governance and identity management) protects organizations from cyber threats that arise when distributed teams access data in the cloud. It ensures secure authentication, central control, and auditing of how applications, DevOps, and automation tools use secrets and privileged credentials to access sensitive resources like databases and cloud environments. Safeguarding your business against cyber risks targeting digital identities is vital.
Identity Security – Essential but Vulnerable

At first glance, the concept seems simple: users need access to corporate systems and applications to perform their roles, and customers need access to web applications to interact with your organization. Identity management plays a crucial role in controlling user access and preventing cybersecurity incidents caused by credential misuse.
Cybercriminals are becoming increasingly skilled at exploiting system vulnerabilities and using social engineering techniques to breach networks and gain access to critical data. These risks are heightened as organizations move to the cloud and pursue digital transformation. In today’s digital world, data is an organization’s most valuable asset, making an identity-centric cybersecurity approach essential to combat evolving identity-based threats.
Attackers typically start by compromising credentials and then escalate their privileges until they access your most sensitive data.
Time for Self-Reflection

How can I address the risks tied to complex identity management projects as our business demands grow?

Am I still struggling to ensure the right access to the right resources at the right time?

Are our identity challenges improving, or are they becoming harder to manage?
How ApeXell Addresses the Identity Security Issue
Even if your organization has invested in identity security tools, these initiatives are often technology-driven or problem-focused, leading to a fragmented set of solutions that may cause chaos within your operations.
ApeXell takes a holistic, strategic approach to the identity security challenge. We work with you to build on existing investments and guide your organization toward a more integrated and strategic identity security model. Together, we will create a bespoke solution that not only supports your organization’s growth but also reduces overall risk.
Privileged Access Management (PAM) and Identity and Access Management (IAM) Work Hand in Hand
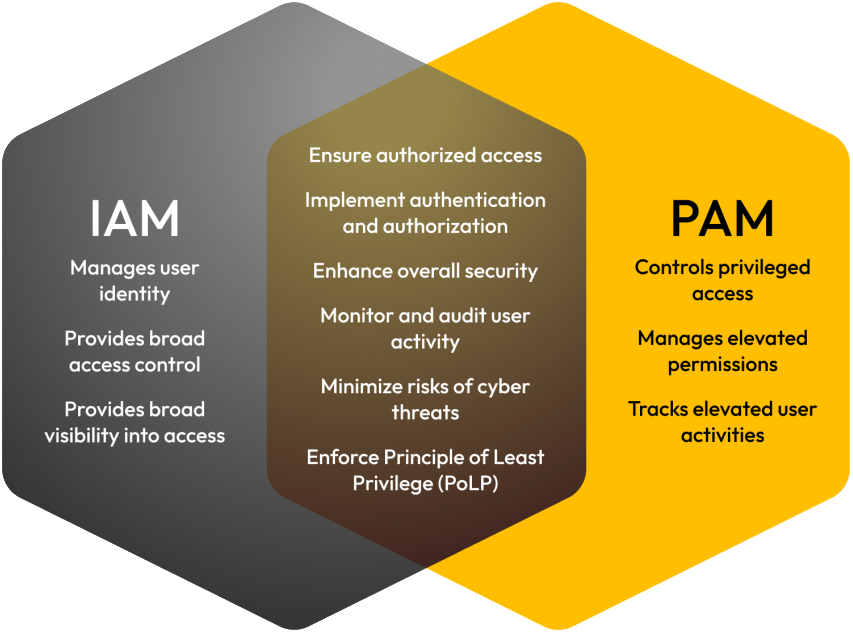
The integration of PAM and IAM enhances your organization’s security posture. These two systems complement and reinforce each other. IAM ensures secure and efficient access for privileged users, while PAM safeguards the credentials of IAM administrators and users with elevated privileges. With single sign-on for initial authentication followed by multi-factor authentication for sensitive access requests, privileged accounts are effectively protected from unauthorized access.
Client Testimonials
What They’re Talking?

Business Developer
Working with ApeXell transformed our approach to cybersecurity. Their team identified critical vulnerabilities and implemented solutions that reduced our risk profile by 60%. They truly set the standard for excellence in this field.

IT Director
The expertise and strategic guidance provided by ApeXell helped us navigate complex compliance challenges. Their proactive approach ensured zero downtime during the transition.

Senior Security Analyst
What sets ApeXell apart is their ability to demystify cybersecurity for teams at all levels. Their workshops equipped us with tools and knowledge to strengthen our internal defenses.

